Creating a seamless access experience with the digital double
A digital double is a proper representation of physical and digital assets. How it fuses identity and personality, and why that’s important. …
Check out all the on-demand sessions from the Intelligent Security Summit here.
Economics in the digital world has evolved in parallel with those of the physical world — moving from a focus on products to services and, now, experiences. Joseph Pine and James Gilmore first introduced the concept in their book[1], “The Experience Economy.” There they observed that “getting personal with customers is the DNA of the Experience Economy.”
As consumers continue to accelerate their adoption of digital technologies, the Experience Economy has become firmly planted in the digital world. And end users have significantly increased their expectations for digital experiences that are tailored to their interests and needs at any given time.
As a result, it has become imperative that organizations deliver digital experiences that are personalized, real-time, geo-sensitive, predictive and omnichannel. Moreover, the teams crafting these digital experiences require a proper methodology to represent personalization attributes firmly and securely in the digital world. The “digital double” is a concept created to address this need.
The idea of a digital double first came to me in the spring of 2016. I was traveling to deliver a keynote at WSO2Con Asia (the APAC edition of WSO2’s yearly user conference) on the topic “Building a Digital Enterprise: Learning from Experience.”
So, I started creating the keynote storyboard on the long flight from San Francisco to Colombo, Sri Lanka. However, the storyline was not coming along the way I had hoped. So, I switched on the onboard entertainment system and came across the movie Tron Legacy, where the characters are pulled into a virtual world. That’s when it hit me: The digital universe requires a proper representation of physical and digital assets, a digital double.
Defining a digital double
There are similar concepts to the digital double, largely fostered by the rapid expansion of the Internet of Things (IoT). Digital twin and digital self are good examples, but they each represent just one type of asset. By contrast, the digital double is a representation of people, places, and things in the digital universe.
Your digital double is always active inside the digital space, regardless of physical activity such as sleeping or watching TV. Not only that, it makes decisions on your behalf. Dating applications are an excellent example for understanding the behavior of a digital double. Once you create a profile in the dating application, your digital double starts dating people on your behalf. As a result, you will miss your first date but get a better match.
Event
Intelligent Security Summit On-Demand
Learn the critical role of AI & ML in cybersecurity and industry specific case studies. Watch on-demand sessions today.
Therefore, as digital craftsmen, we must protect the digital doubles we create inside digital applications by applying fundamentals — such as privacy, trust, confidentiality, and security controls — enhancing security through a privacy ecosystem and regulations to protect the digital double against cyber threats.
Identity vs. personality
In understanding the digital double, it’s important to recognize the difference between identity and personality. Identity is what sets you apart from others and makes you unique. Personality is how you describe yourself; it is your sense of humor, your emotions, and how you react in different situations. Identity verification establishes that it is you using a particular system, but the system knows nothing about you other than a few identity attributes. Until the system knows your personality, it cannot get to know you, and it cannot offer a personalized experience.
“Identity in the form of continuity of personality is an extremely important characteristic of the individual.” ~Kenneth Lee Pike, anthropologist.
Customer identity and access management (CIAM) is the way to intimate personalization. CIAM today is mostly about access control, but CIAM in the future will blend customer personality into the business.
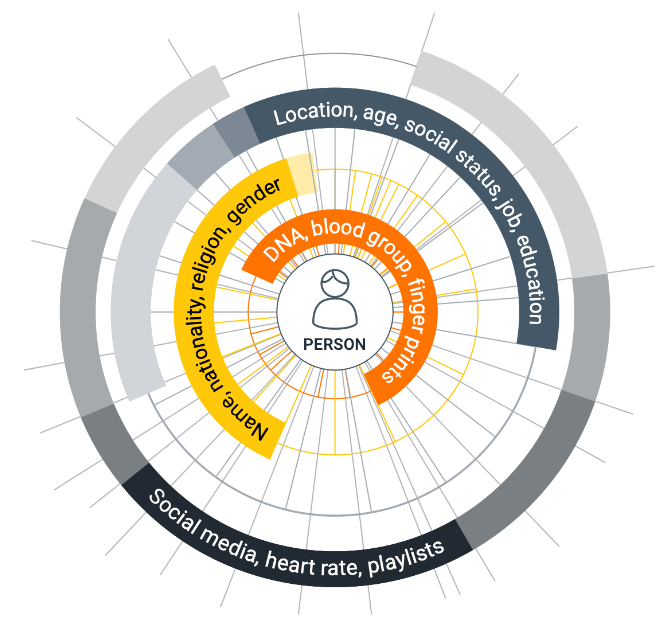
Identity and personality attributes vary in durability. These attributes can be categorized based on how often they change.
- Never change: DNA, blood group, fingerprints;
- Rarely change: Name, nationality, religion, gender;
- Frequently change: Location, age, social status, job, education;
- Rapidly change: Social media, heart rate, playlists.
Connecting the dots
The digital double is the fusion of your identity and personality. As we discussed earlier, the digital double represents the digital universe’s people, places, and things. Moreover, the digital double holds the identity and personality attributes with it. However, representing, storing, and exposing these attributes is challenging due to the dynamic nature of both identity and personality attributes. The World Wide Web Consortium (W3C) has established the foundation for a solution to this problem by introducing the decentralized identifiers (DID) specification, which addresses the core architecture, data model, and representations of identity and personality attributes.
The digital double is changing traditional digital identity representation by moving from geocentric (owned and managed by the identity provider) to heliocentric (owned and managed by the individual). The heliocentric nature is an excellent way to handle content management, and compliance requirements must be addressed when accessing and storing identity and personality attributes.
In addition, the dynamic nature of these attributes makes the digital double adaptive and decentralized, which the industry is trying to address through an identity fabric concept that comes with Web 3.0. My preference is to call the distributed identity network an “Identity mesh” similar to other distributed and cloud-native architecture styles such as service mesh, data mesh and event mesh. Unfortunately, there is no unique identifier for the digital assets in the digital ecosystem; therefore, a digital double has to be highly interoperable across various digital identity representations.
CIAM is the foundation
CIAM is the foundation that creates and manages the digital double. Hence, the CIAM provider has to consider this and provide the digital double as a service to ease application development. To do so, the CIAM provider needs to incorporate a new set of capabilities in addition to the core identity and security features, such as authorization and authentication in full power. CIAM systems are already capturing identity attributes from defined policy information points (PIPs).
Furthermore, the CIAM provider has to introduce application programming interfaces (APIs) and event syncs to capture and record personalization attributes based on user activities from various sources. This is predominantly interaction data from omnichannel applications and transactions from systems of records. In addition, the CIAM system will silently observe the customer by monitoring their social media posts, including sentiment analysis, and detect interaction patterns and anomalies. The CIAM system will then trigger alerts when anomalies are detected.
Once customers’ attributes are captured, the CIAM provider has to enable APIs that enable applications to query the attributes and use them in the digital experiences delivered by the app. Therefore, graph APIs based on GraphQL are vital for implementing attribute retrieval APIs. Additionally, artificial intelligence (AI) and machine learning (ML) processes can associate with the attribute data store and deliver insights on behalf of the business. The extended capabilities listed above let the CIAM provider combine the attributes of a digital double across the business to build a comprehensive personality profile.
Path to creating a seamless access experience with the digital double
The business and its CIAM provider must collaborate to achieve a seamless access experience with the digital double. The CIAM provider has to enable the extended capabilities discussed in the previous section, and the business needs to leverage those capabilities in the application architecture and development.
The end result cannot be achieved overnight. However, the following five-step CIAM maturity model can help the organization and CIAM provider make iterative but steady progress.
- Level 0 — None: Customers are strangers, and interactions are anonymous.
- Level 1 — Managed: Basic identity management, registration, password management and user management.
- Level 2 — Siloed: Simple integration with siloed business systems, customer information replicated within apps.
- Level 3 — Connected: Business systems integration, 360° customer view, omnichannel customer experience.
- Level 4 — Optimized: Intelligent, adaptive, and personalized customer experience.
From the business point of view, the organization achieves CIAM 1.0 once they have access management and identify a person as outlined for levels 1 (Managed) and 2 (Siloed). Next, the organization will move to CIAM 2.0 by integrating the user’s identity into the business, as described in level 3 (Connected). Finally, the organization will graduate to CIAM 3.0 by enhancing business applications to know each person as noted in level 4 (Optimized).
Final thoughts
We mainly reviewed customer-focused personalization using business-to-consumer (B2C) CIAM, but as a digital craftsman, you have to build digital experiences for other types of users. The same concept can be extended to other business models using CIAM, including business-to-business (B2B) CIAM for handling partners and suppliers and business-to-employee (B2E) CIAM for managing employees.
Getting personal with customers is the DNA of the experience economy, and in the digital world, CIAM is the way to initiate personalization. Moreover, because the digital double is the fusion of each person’s identity and personality, CIAM is needed to provide the foundation that creates and manages the digital double. To use this capability in application development, the CIAM provider has to enable the digital double as a service. The CIAM maturity model can be used as a steady, iterative, and frictionless path to creating a seamless access experience with the digital double.
Asanka Abeysinghe is chief technology evangelist at WSO2.
[1] Ii, J. P. B., & Gilmore, J. H. (2019). The Experience Economy, With a New Preface by the Authors: Competing for Customer Time, Attention, and Money (Revised). Harvard Business Review Press.
DataDecisionMakers
Welcome to the VentureBeat community!
DataDecisionMakers is where experts, including the technical people doing data work, can share data-related insights and innovation.
If you want to read about cutting-edge ideas and up-to-date information, best practices, and the future of data and data tech, join us at DataDecisionMakers.
You might even consider contributing an article of your own!